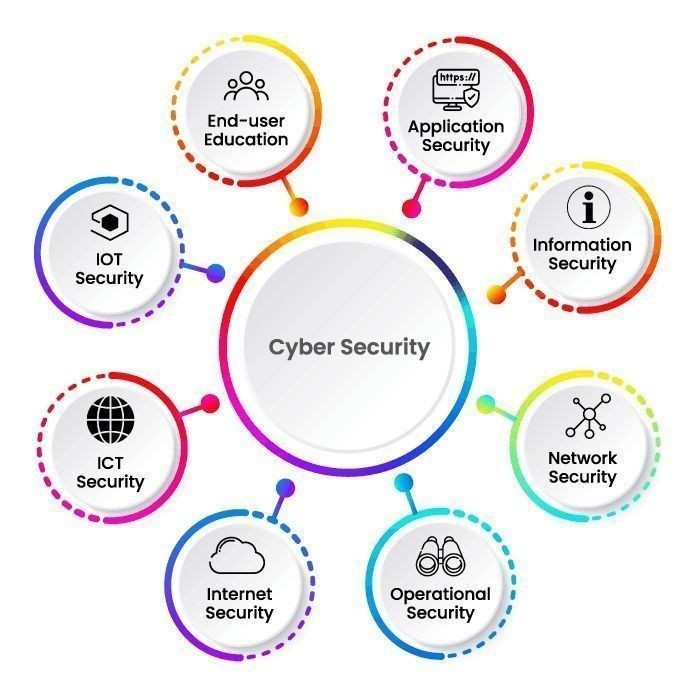
Cybersecurity & Network Security
Cybersecurity and Network seccurity most important in our life.With cyber threats evolving rapidly, businesses must prioritize cybersecurity and network security to safeguard sensitive data, prevent breaches, and maintain trust.
Explore more at Red9Systech Cybersecurity Guide.
What is Cybersecurity & Network Security?
Cybersecurity
🔹 Protects data, systems, and networks from cyber threats.
🔹 Includes encryption, firewalls, antivirus software, and threat detection.
Network Security
🔹 Focuses on securing network infrastructure from attacks.
🔹 Involves firewalls, intrusion detection systems (IDS), and VPNs.
Learn more at Cybersecurity Basics.
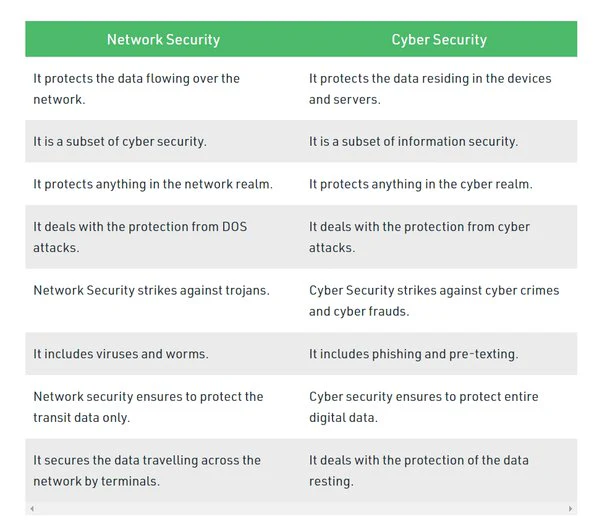
Common Cybersecurity Threats
1. Phishing Attacks
Fake emails trick users into revealing sensitive information.
2. Ransomware
Malware that encrypts files and demands ransom for decryption.
3. DDoS Attacks
Floods networks with traffic, making services unavailable.
4. Insider Threats
Employees or contractors who misuse access to steal data.
Learn how to prevent cyber attacks.
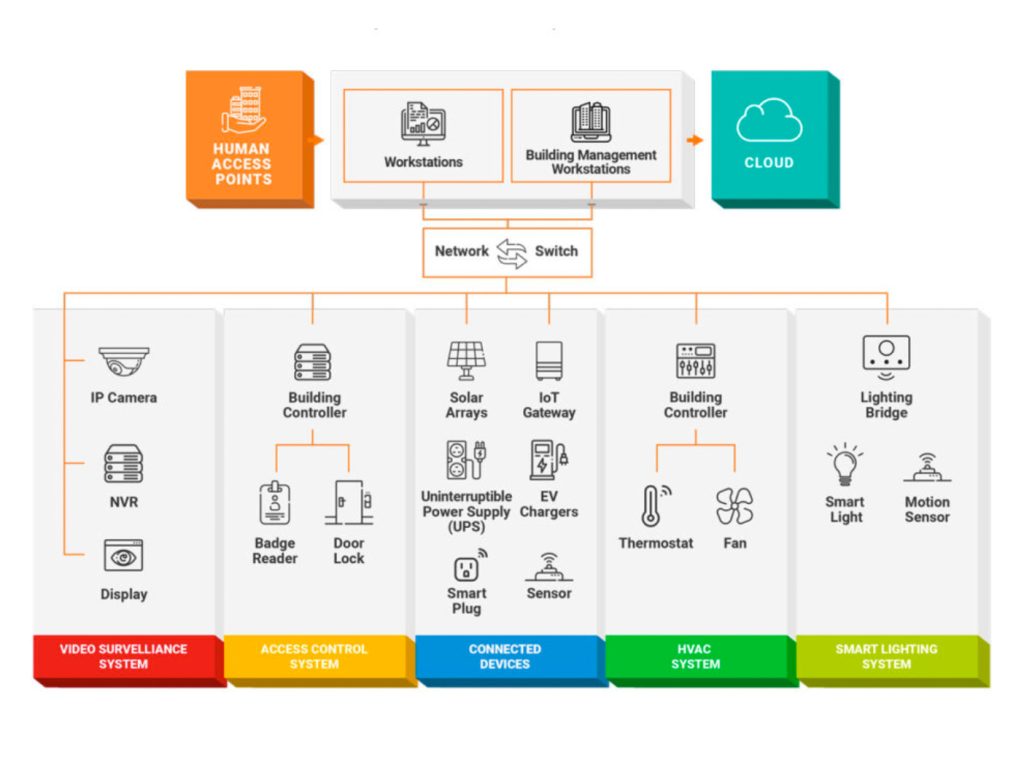
Best Practices for Cybersecurity & Network Security
1. Use Multi-Factor Authentication (MFA)
Adds an extra layer of security beyond passwords.
2. Regular Software Updates
🔹 Patches vulnerabilities to prevent cyber attacks.
3. Implement Firewalls & Intrusion Detection
Blocks malicious traffic and detects threats in real time.
4. Data Encryption
Ensures sensitive information remains unreadable to hackers.
5. Cybersecurity Awareness Training
Educates employees on identifying and preventing cyber threats.

Emerging Trends in Cybersecurity
AI & Machine Learning for Threat Detection
Zero Trust Security Models to verify every user and device.
Cloud Security as more businesses move to cloud-based environments.
Blockchain for Secure Transactions & Identity Management.
Read about Future of Cybersecurity.